本文最后更新于5 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
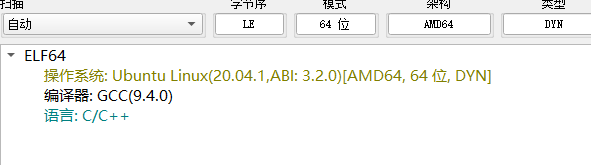
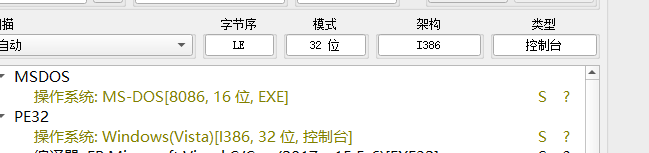
魔改的upx壳,我不会脱,工具脱壳、
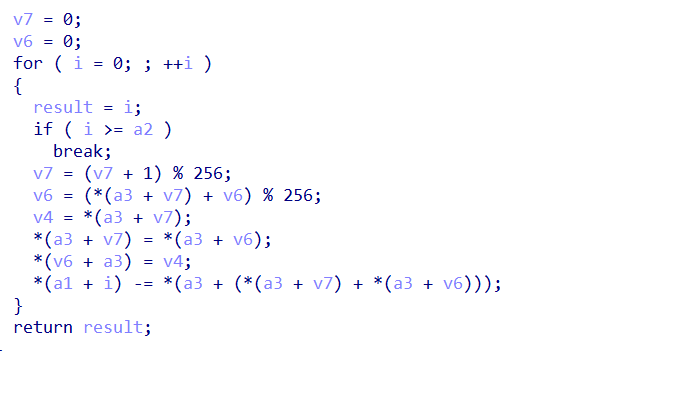
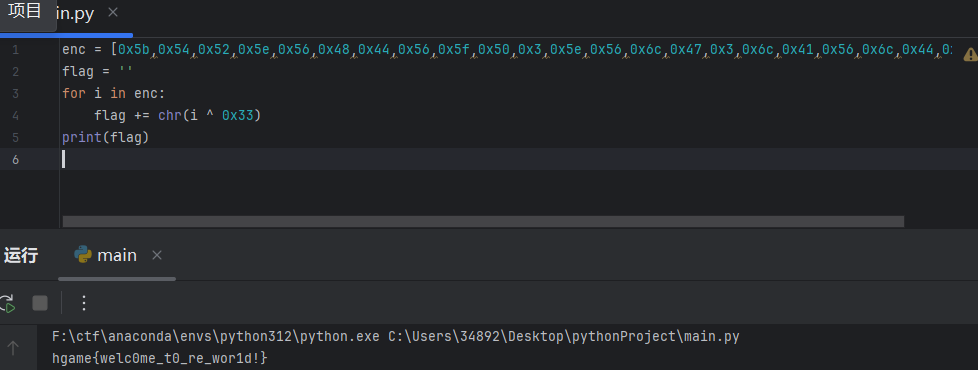
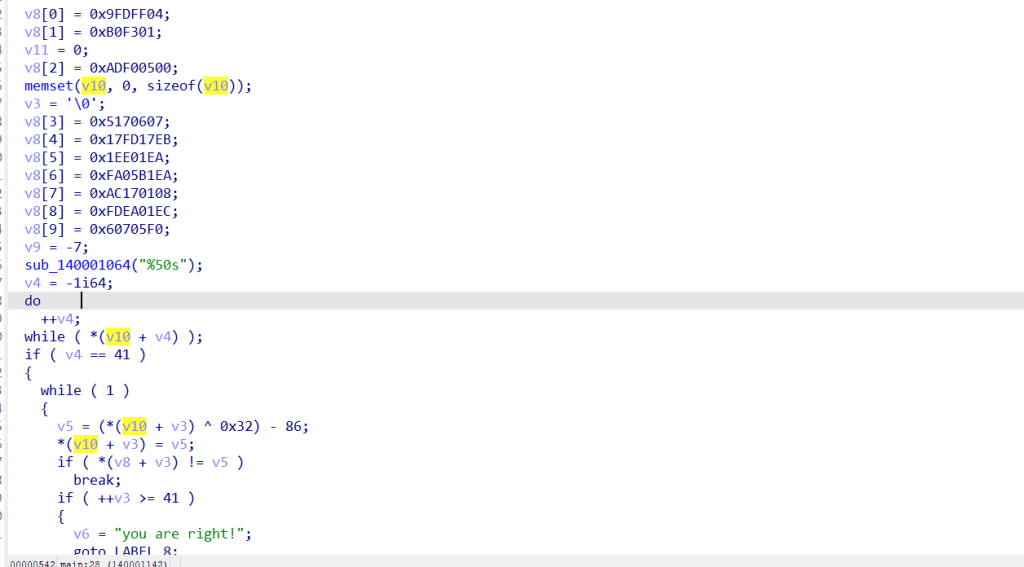
里面是一个魔改的rc4(异或变成了减号),key的解密也是rc4,我用的动调获取
解密脚本
include
include
define SBOX_SIZE 256
// RC4初始化函数,生成密钥流
void rc4_init(unsigned char *key, int key_length, unsigned char *S) {
int i, j = 0;
unsigned char temp;
// 初始化S盒
for (i = 0; i < SBOX_SIZE; i++) {
S[i] = i;
}
// 使用密钥对S盒进行置换
for (i = 0; i < SBOX_SIZE; i++) {
j = (j + S[i] + key[i % key_length]) % SBOX_SIZE;
// 交换S[i]和S[j]
temp = S[i];
S[i] = S[j];
S[j] = temp;
}
}
// RC4加解密核心算法
void rc4_crypt(unsigned char *data, int data_length, unsigned char *S) {
int i = 0, j = 0, k;
unsigned char temp, keystream;
for (k = 0; k < data_length; k++) {
i = (i + 1) % SBOX_SIZE;
j = (j + S[i]) % SBOX_SIZE;
// 交换S[i]和S[j]
temp = S[i];
S[i] = S[j];
S[j] = temp;
// 生成密钥流
keystream = S[(S[i] + S[j]) % SBOX_SIZE];
// 对数据进行异或解密
data[k] += keystream;
}
}
int main() {
// 密钥 (可以根据需要更改)
unsigned char key[] = "ecg4ab6";
int key_length = strlen((char *)key);
// 要解密的密文
unsigned char ciphertext[] = { 0xF8, 0xD5, 0x62, 0xCF, 0x43, 0xBA, 0xC2, 0x23, 0x15, 0x4A,
0x51, 0x10, 0x27, 0x10, 0xB1, 0xCF, 0xC4, 0x09, 0xFE, 0xE3,
0x9F, 0x49, 0x87, 0xEA, 0x59, 0xC2, 0x07, 0x3B, 0xA9, 0x11,
0xC1, 0xBC, 0xFD, 0x4B, 0x57, 0xC4, 0x7E, 0xD0, 0xAA, 0x0A}; // 假设这是加密后的数据
int ciphertext_length = sizeof(ciphertext);
// 初始化S盒
unsigned char S[SBOX_SIZE];
// 初始化RC4
rc4_init(key, key_length, S);
// 解密密文
rc4_crypt(ciphertext, ciphertext_length, S);
// 输出解密后的数据
printf("Decrypted text: ");
for (int i = 0; i < ciphertext_length; i++) {
printf("%c", ciphertext[i]);
}
printf("\n");
return 0;
}
hgame{Y0u’r3_re4l1y_g3t_0Ut_of_th3_upX!}