本文最后更新于5 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
die查一下,无壳32位
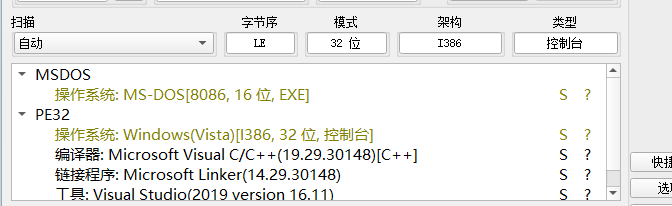
主函数长这样

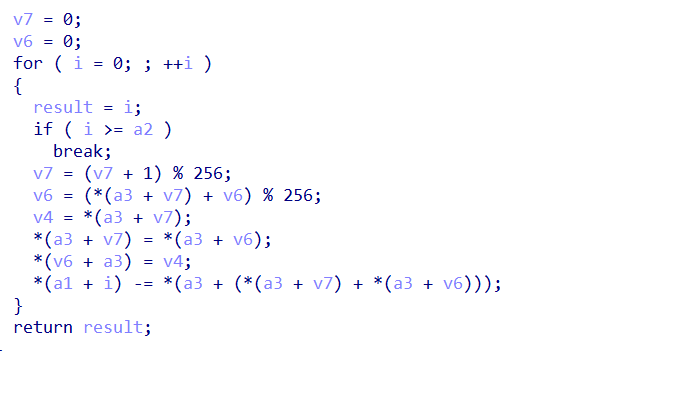
sub_411523是一个tea加密

解一下得到值
脚本附上
from ctypes import *
from Crypto.Util.number import long_to_bytes
key = [0x12, 0x34, 0x56, 0x78]
enc = [0x60FCDEF7, 0x236DBEC]
for i in range(0, len(enc), 2):
v0 = c_uint32(enc[i])
v1 = c_uint32(enc[i + 1])
delta = 0x61C88647
sum = c_uint32(-delta * 32)
r = 32
for j in range(r):
v1.value -= (sum.value + v0.value) ^ (key[2] + 16 * v0.value) ^ (key[3] + (v0.value >> 5))
v0.value -= (sum.value + v1.value) ^ (key[0] + 16 * v1.value) ^ (key[1] + (v1.value >> 5))
sum.value += delta
enc[i] = v0.value
enc[i + 1] = v1.value
# 以十六进制格式输出加密结果
print(f"{enc[i]:08X}", end=" ")
print(f"{enc[i + 1]:08X}", end=" ")往下走一路点点点,有一个smc

a1的值就是v10=v11=v7
前面tea加密解出来等于3,写一个smc脚本


从0041D000到0041E600
smc脚本
for i in range(0x41d000,0x41E600):
patch_byte(i,get_wide_byte(i)^3)

是个rc4,key是you_are_master
动调提个数据


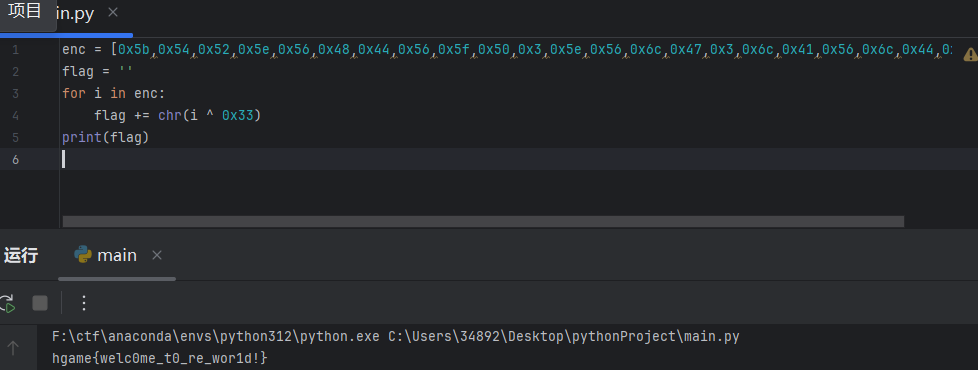
拿下flag
HDCTF{y0u_ar3_rc4_t3a_smc_m4ster!!}
rc4脚本附上
from base64 import *
def KSA(key):
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
return S
def PRGA(S):
i, j = 0, 0
while True:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
K = S[(S[i] + S[j]) % 256]
yield K
def RC4Decrypt(key, text):
S = KSA(key)
keystream = PRGA(S)
res = []
for char in text:
res.append(char ^ next(keystream))
return bytes(res)
key = b'you_are_master'
plaintext = [ 0x0F, 0x94, 0xAE, 0xF2, 0xC0, 0x57, 0xC2, 0xE0, 0x9A, 0x45,
0x37, 0x50, 0xF5, 0xA0, 0x5E, 0xCB, 0x2C, 0x16, 0x28, 0x29,
0xFE, 0xFF, 0x33, 0x46, 0x0E, 0x57, 0x82, 0x22, 0x52, 0x26,
0x2B, 0x6E, 0xE4, 0x82, 0x24]
Rc4encrypt = RC4Decrypt(key, plaintext)
print(Rc4encrypt.decode())