本文最后更新于5 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
die查一下,无壳32位
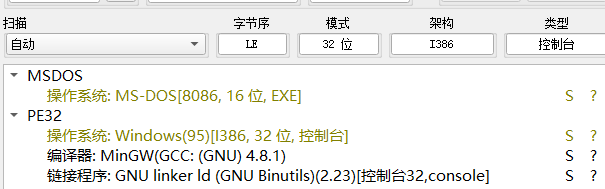
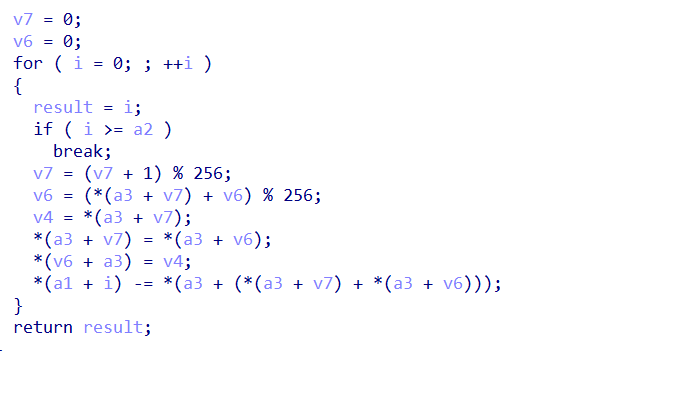
逻辑很简单,就是输入经过加密然后与比较验证

加密逻辑在sub_401520
int __cdecl sub_401520(_BYTE *a1, int a2)
{
_BYTE *v2; // ebp
_BYTE *v3; // ecx
int v4; // ebx
int v5; // eax
int i; // edx
_BYTE *v7; // edx
int j; // ecx
_BYTE *v9; // ecx
int k; // ebx
int v12; // [esp+0h] [ebp-38h]
int v13; // [esp+4h] [ebp-34h]
int v14; // [esp+Ch] [ebp-2Ch]
int __cdecl sub_401520(_BYTE *a1, int a2)
{
_BYTE *v2; // ebp
_BYTE *v3; // ecx
int v4; // ebx
int v5; // eax
int i; // edx
_BYTE *v7; // edx
int j; // ecx
_BYTE *v9; // ecx
int k; // ebx
int v12; // [esp+0h] [ebp-38h]
int v13; // [esp+4h] [ebp-34h]
int v14; // [esp+Ch] [ebp-2Ch]
if ( !*a1 )
return 0;
v2 = a1 + 4;
v3 = a1;
v4 = 0;
v5 = 0;
v13 = 0;
while ( 1 )
{
v14 = -1;
for ( i = 0; i != 64; ++i )
{
while ( aAbcdefghijklmn[i] != *v3 )
{
if ( ++i == 64 )
goto LABEL_7;
}
LOBYTE(v14) = i;
}
LABEL_7:
LOBYTE(i) = 0;
do
{
while ( aAbcdefghijklmn[i] != a1[v4 + 1] )
{
if ( ++i == 64 )
goto LABEL_11;
}
BYTE1(v14) = i++;
}
while ( i != 64 );
LABEL_11:
v7 = &a1[v4 + 2];
for ( j = 0; j != 64; ++j )
{
while ( aAbcdefghijklmn[j] != *v7 )
{
if ( ++j == 64 )
goto LABEL_15;
}
BYTE2(v14) = j;
}
LABEL_15:
v9 = &a1[v4 + 3];
for ( k = 0; k != 64; ++k )
{
while ( aAbcdefghijklmn[k] != *v9 )
{
if ( ++k == 64 )
goto LABEL_19;
}
HIBYTE(v14) = k;
}
LABEL_19:
v12 = v5 + 1;
*(a2 + v5) = (4 * HIBYTE(v14)) | (BYTE2(v14) >> 4) & 3;
if ( *v7 == 61 )
return v12;
v12 = v5 + 2;
*(a2 + v5 + 1) = (16 * BYTE2(v14)) | (BYTE1(v14) >> 2) & 0xF;
if ( *v9 == 61 )
return v12;
v5 += 3;
v3 = v2;
v2 += 4;
v13 += 4;
v4 = v13;
*(a2 + v5 - 1) = (BYTE1(v14) << 6) | v14 & 0x3F;
if ( !*(v2 - 4) )
return v5;
}
}if ( !*a1 )
return 0;
v2 = a1 + 4;
v3 = a1;
v4 = 0;
v5 = 0;
v13 = 0;
while ( 1 )
{
v14 = -1;
for ( i = 0; i != 64; ++i )
{
while ( aAbcdefghijklmn[i] != *v3 )
{
if ( ++i == 64 )
goto LABEL_7;
}
LOBYTE(v14) = i;
}
LABEL_7:
LOBYTE(i) = 0;
do
{
while ( aAbcdefghijklmn[i] != a1[v4 + 1] )
{
if ( ++i == 64 )
goto LABEL_11;
}
BYTE1(v14) = i++;
}
while ( i != 64 );
LABEL_11:
v7 = &a1[v4 + 2];
for ( j = 0; j != 64; ++j )
{
while ( aAbcdefghijklmn[j] != *v7 )
{
if ( ++j == 64 )
goto LABEL_15;
}
BYTE2(v14) = j;
}
LABEL_15:
v9 = &a1[v4 + 3];
for ( k = 0; k != 64; ++k )
{
while ( aAbcdefghijklmn[k] != *v9 )
{
if ( ++k == 64 )
goto LABEL_19;
}
HIBYTE(v14) = k;
}
LABEL_19:
v12 = v5 + 1;
*(a2 + v5) = (4 * HIBYTE(v14)) | (BYTE2(v14) >> 4) & 3;
if ( *v7 == 61 )
return v12;
v12 = v5 + 2;
*(a2 + v5 + 1) = (16 * BYTE2(v14)) | (BYTE1(v14) >> 2) & 0xF;
if ( *v9 == 61 )
return v12;
v5 += 3;
v3 = v2;
v2 += 4;
v13 += 4;
v4 = v13;
*(a2 + v5 - 1) = (BYTE1(v14) << 6) | v14 & 0x3F;
if ( !*(v2 - 4) )
return v5;
}
}看得出来是一个base64的编码,表没变
把字符进行base64编码

解出来的这一坨是错的(后面做不出来看wp才知道)
这里的传递方法变了
先传进来的高位,字符放在了低位的地方
而低位放在高位,然后base64
因此解出来的那一坨要每4个字符逆序处理
因此应该长这样Y0uReallyKn0wB4s

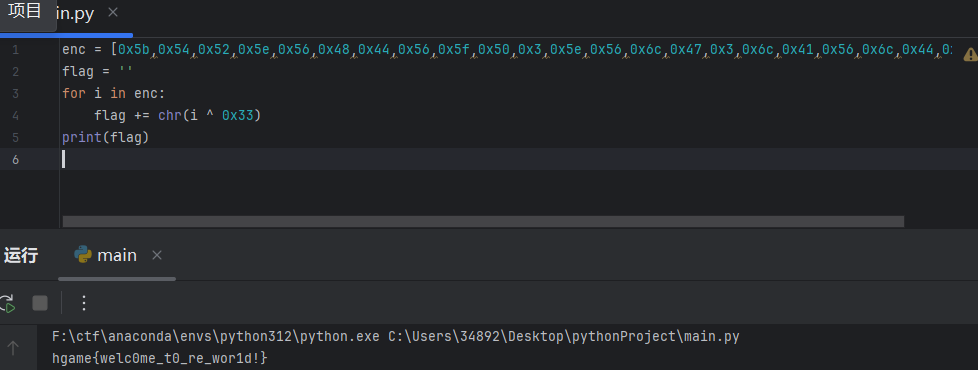
根据题目描述要加3个=,已知flag长度是20位,所有还需要根据md5值爆破最后一位

最后一位是3
这道题表和明文什么的都是直接给的,不要慢慢找,但我对base64不是很熟悉,导致逆序我没有发现,通过md5值进行爆破我也是第一次见